AI Safety for Families & Schools
Digital Security and IT Management for Families and Schools.
Watch What We're About
Automate Tedious Tasks and Enhance Digital Security
Get to know us and learn about the limitless ways we help you meet your digital needs, from streamlining IT management or HR tasks in your company to ensuring your children or students’ digital safety.
To Help You
Protect, Educate, Moderate
Everything you need to monitor, manage, and protect your team, whether it’s your family, students, or employees.
Parental Controls
Monitor and manage your child’s online activity and protect them from the dangers of the digital world.
School Digital Safety
Maximize your students’ productivity by setting rules and limits on their digital devices.
School Management
Simplify the supervision and management of each and every device at your school.
What We Have to Offer
Safety, Efficiency, Simplicity
No matter the size of your family, school, or company, we are here to help you keep them safe and under control.

Shield Your Family from Digital Threats
- Encourage healthy device usage habits by setting screen time limits on your little one’s devices
- Block inappropriate websites and search results on your child’s electronic devices
- Monitor children’s social activity on apps like Instagram, TikTok, WhatsApp, and more
- Locate your kids wherever they go, even when you’re not around
- Receive full reports of your child’s digital activity on all devices
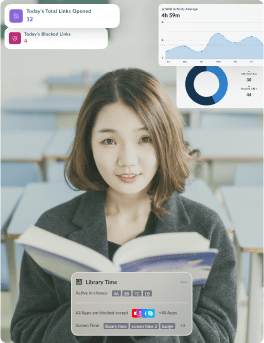
Boost Your Students’ Productivity
- Detect and address inappropriate behavior by students on social media platforms like TikTok, WhatsApp, etc.
- Eliminate excessive device usage by limiting the time students spend on their phones
- Get notified the moment students get in or out of school
- Remove distractions by disabling addictive games and apps
- Filter out inappropriate websites and content on the internet

Shield Your Family from Digital Threats
- Encourage healthy device usage habits by setting screen time limits on your little one’s devices
- Block inappropriate websites and search results on your child’s electronic devices
- Monitor children’s social activity on apps like Instagram, TikTok, WhatsApp, and more
- Locate your kids wherever they go, even when you’re not around
- Receive full reports of your child’s digital activity on all devices

Boost Your Students’ Productivity
- Detect and address inappropriate behavior by students on social media platforms like TikTok, WhatsApp, etc.
- Eliminate excessive device usage by limiting the time students spend on their phones
- Get notified the moment students get in or out of school
- Remove distractions by disabling addictive games and apps
- Filter out inappropriate websites and content on the internet
What Makes Us Different
Where Creativity Streamlines Security
Get to know us by learning more about our vision, our ambition, and the things we made our mission.
Protection
We made it our mission to help every family, school, and company keep their little ones, students, and assets safe in the digital world.
Innovation
Striving to stay ahead of the curve, we continuously come up with cutting-edge solutions that meet the ever-changing needs of our customers.
Automation
Aiming to keep things as simple and cost-effective as possible for our customers, we value nothing more than the automation of our services.
Pharetra dictumst
Convallis ullamcorper donec accumsan commodo auctor pharetra gravida eu. Feugiat malesuada vulputate pellentesque est neque.
Pharetra dictumst
Neque ornare eu ultricies ut. Tellus etiam feugiat lectus morbi sagittis.
Pharetra dictumst
Molestie imperdiet imperdiet nisl rutrum nibh platea. Rutrum dignissim ut ornare enim egestas ultricies.
About Us
Our Way
Surveying hundreds of families, schools, and companies, our team curated our products to be as user-friendly and simple as possible.
Constantly improving our services with the latest security updates, we pride ourselves on the safety of our products.
Striving for the perfect balance between quality and affordability, we ensure our customers get the most out of our services without breaking the bank.
Contact Us
What Others Say About SternX
Blog & News
CHECK OUT THE LATEST BLOG ARTICLES
News, Articles, and Top Stories for Parents, Teachers, School Officials, and IT Managers.
Importance of Cybersecurity for Business in the Digital Age
Businesses rely heavily on digital technologies, and the importance of cybersecurity for business cannot be overstated. As our reliance on technology grows, so do the risks associated with cyber threats. Cybercriminals are becoming increasingly sophisticated,

Sexting: Dangers of Sexting in Schools & Preventive Measures
In the age of technology and social media, the dangers of sexting in schools among students have become a growing concern for educators, parents, and the community. Sexting, the act of sending or receiving sexually explicit or semi-nude images, messages, or
Classroom Management Software for Schools: Tools & Resources
Effective classroom management has become a crucial aspect of ensuring a productive and engaging learning experience for students. Classroom management software has emerged as a powerful tool to assist teachers in maintaining order, monitoring student